Secure software development is no longer a luxury. And but rather a requirement in the fast-paced digital environment where data breaches and cyber attacks are a constant concern. Choosing the proper suppliers to collaborate with is a wise strategic decision for companies.
1. Put Security First from the Start

Security should not be treated as an afterthought, but rather as a fundamental aspect of your software. When you hire vetted developers, make sure they share your commitment to your security strategy.
Ask them about their:
- best practices;
- security standards;
- capacity to integrate security measures at each stage of the development lifecycle.
2. Experience and Knowledge
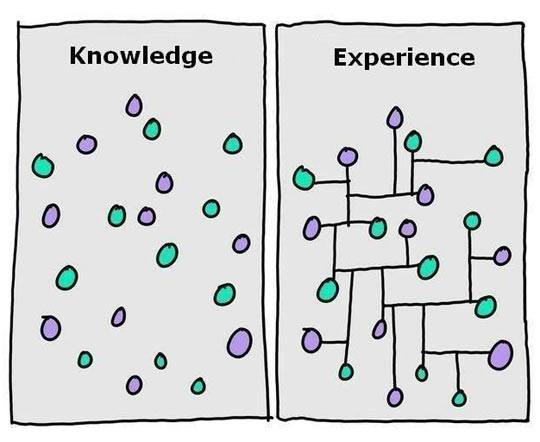
The track record of a seller is quite telling. Explore:
- experience creating safe software;
- the variety of businesses they have worked with;
- the difficulty of the projects they have taken on.
A provider with a track record of providing security solutions is a great asset since experience generates insight.
Recommended reading: Developer Experience: The Vital Role of Prioritization in IT Teams
3. Requirements and Certifications

A vendor’s dedication to data protection is confirmed by security standards and certifications. Ask if the company complies with laws like:
- the GDPR;
- the HIPAA;
- standards that are relevant to your business.
Certifications like ISO 27001 show how committed a provider is to maintaining reliable security procedures.
FURTHER READING: |
| 1. The 6 Steps of Software Product Development Life Cycle |
| 2. 5 Software Developer Skills Wish They Had Learned in College |
4. Vulnerability Control
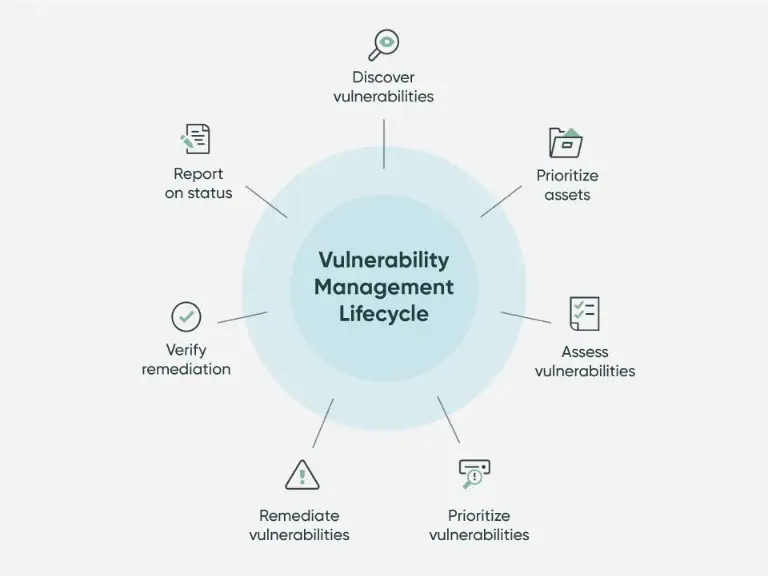
Vulnerability management must be proactive if prospective threats are to be stopped. Throughout the lifespan of the program, a trustworthy vendor should have a well-defined procedure for finding, evaluating, and fixing vulnerabilities.
FURTHER READING: |
| 1. How to Manage Time Effectively for Assignments? |
| 2. 4 Best Web Scraping Projects To Automate Your Work & Life In 2023 |
5. Safe Coding Techniques
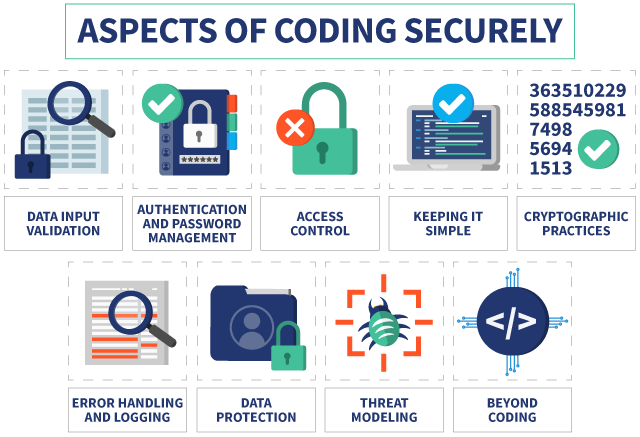
The code itself is the basis for secure software. Explore the vendor’s coding procedures, such as code reviews, testing procedures, and vulnerability evaluations. A vendor that follows safe coding guidelines aids in preventing vulnerabilities from entering your program.
6. Data Security and Confidentiality

Since data breaches often make the news, data security is crucial. Analyze the vendor’s methods for protecting private data both during development and after launch. A security-conscious provider will have strict access restrictions, strong encryption procedures, and data anonymization.
FURTHER READING: |
| 1. 5 Simple Tips to Hire a Mobile App Developer in 2023 |
| 2. Hiring a Freelancer vs Agency for Software Development |
7. SDLC: Secure Development Lifecycle
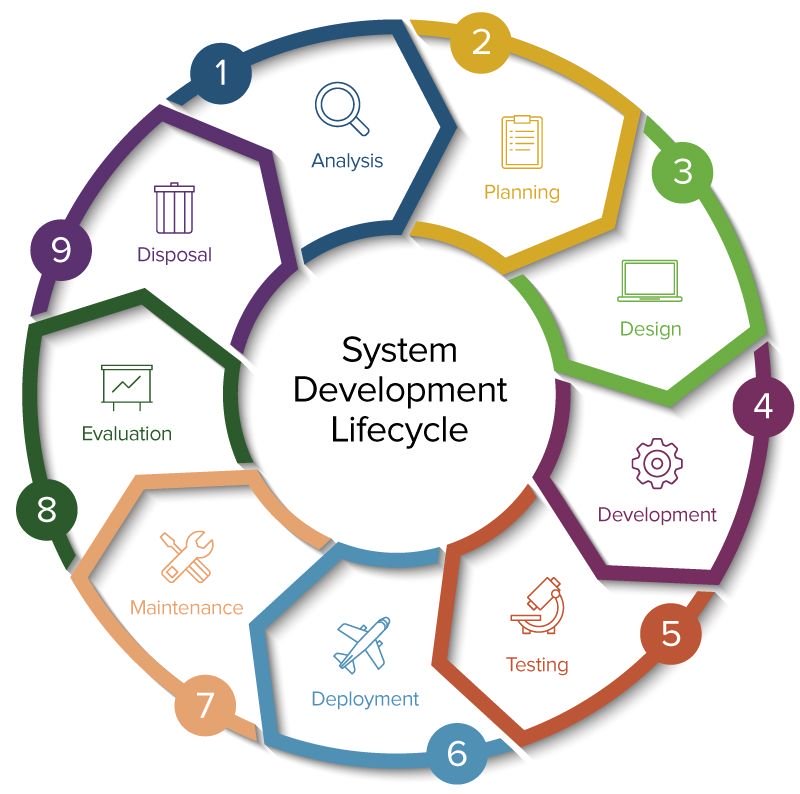
Security is easily included in each stage of development in an efficient SDLC. Ask about the SDLC process used by the vendor, including requirements analysis, testing, and deployment. Security protections will advance together with your program thanks to a solid SDLC.
8. Ethical Hacking and Penetration Testing

Penetration testing and ethical hacking are litmus tests for your software’s resilience since they simulate real-world assaults. A provider demonstrates a commitment to security. He does thorough testing to find vulnerabilities and aggressively fix them.
9. Response to Incidents and Recovery
Rapid and successful incident response is essential in the event of a security breach. Evaluate the vendor’s capacity to identify and control breaches, incident response plan, and strategy for returning things to normal.
10. Updates and Continuous Monitoring
Security is a process that never stands still. Ask the vendor how they handle patch management, ongoing monitoring, and timely updates. Regular security updates guarantee that your software is robust to new attacks.
11. References and Testimonials from Clients
Customers are often the greatest judges of a vendor’s reputation. Look for comments and references from previous customers who may provide light on the vendor’s security procedures, communication style, and overall project experience.
12. Transparency and Dialogue
Secure software development is held together by effective communication. Explore:
- the vendor’s channels for communication;
- readiness to provide updates;
- openness to exchanging security-related information.
13. Budgetary Factors

Budgetary restrictions are a fact of life, notwithstanding how vital security is. Make sure the vendor’s price is within your spending limit while retaining essential security measures.
A terrific find is a vendor that manages to mix affordability with high security.
Conclusion
The vendor you choose is a crucial partner in reinforcing your digital fortress in the complex world of safe software development. You may establish a relationship that not only maintains the security of your software. But also sets the road for innovation, development, and a robust digital future by carefully assessing prospective suppliers by these extensive criteria.