Web app attacks are among the main culprits behind data disclosure, regardless of business sizes, industries, or regions. This was proven by the official figures of the 2021 Verizon Report. To avoid such threats, it’s urgent for companies to closely look at security methods when developing a web app. Designveloper, in this article, will focus on the following key points to help you better understand web application security: Definition, Major Threats, and Best Practices.
Web Application Security: Definition and Importance
The coming of dynamic websites has boosted their frequent interactions with visitors. Unlike static counterparts, they allow visitors to provide personal information for different activities therein like sign-up or payments. However, this also poses a perennial problem commonly known as Security.
Today, websites and web apps get more and more complex as cloud computing emerges and develops. Companies tend to store even sensitive data on the cloud because it’s convenient and low-cost. Therefore, security-related issues become an inevitable concern instead of a luxury option.

So, what is web application security exactly? As a subsegment of information security, it includes everything to protect web apps from malicious code and other cyber-attacks. Particularly, companies apply all practices, policies, procedures, and even technologies to secure confidential data against hackers in Internet and web app systems.
User data is not the only reason for companies to develop and deploy security methods. Well-secured web apps can bring visible benefits as follows:
- avoid revenue loss that may be triggered by service downtime, outages and incurred costs for repair and maintenance;
- boost a company’s online reputation and customer trust;
- guarantee web apps comply with security standards (e.g. ISO/IEC 27001 or HIPPA) regulated by local governments or international entities.
Top 10 Web Application Security Threats
Unlike traditional desktop-based software, web apps aren’t limited to any device because they operate on web servers. This contributes to the growing prevalence of web apps. But they concurrently face an increasing number of cyberattacks and threats, as reported by CVE Details. Among them, however, the OWASP warned developers and companies to focus on the top ten flaws:

1. Broken Access Control
Properly configured web apps control user access to authorized functions. However, when broken access control occurs, hackers can act beyond their allowable limits. Accordingly, they easily approach, modify, leak or destroy all data and files they’re not supposed to access.
94% of tested web apps by the OWASP reported this flaw. And it had the highest frequency with over 318,000 occurrences in 2021, according to the Common Weakness Enumerations (CWEs).
2. Cryptographic Failures
Another notable vulnerability Designveloper wants to mention is cryptographic failures, previously called “Sensitive Data Exposure”. This security risk arises when web apps use weak cryptographic algorithms such as SHA-1 or RIPEMD160. Particularly, such functions inadequately protect unauthorized users from accessing or destroying sensitive data in transmission and at rest.
3. Injection
Injecting malicious code into web apps is another common way for attackers to implement unintended queries or commands and access confidential data. SQL injection, Cross-site Scripting (XSS), or OS command are some most common techniques to incur this flaw. This failure is mainly due to neither checking, filtering nor sanitizing user data.
FURTHER READING: |
1. Web Application Examples and Definition for Beginners |
|
4. Insecure Design
Insecure design is a newly-added vulnerability in the OWASP list of web application security risks. It’s about failures to create secure architecture and design principles or patterns.
This failure should be distinguished from development-related flaws which arise during the project development process. Even no matter how the development process is perfect, products with insecure designs are prone to attacks. This is because developers are not well-instructed to build essential security controls.
Therefore, to avoid this failure, your company needs to establish a business risk profile. This document determines required risk levels and opportunities to help prioritize major threats.
5. Security Misconfiguration
This security risk occurs when web apps use insecurely configured features, insecure headers, insecure default passwords and accounts, and more. Security misconfiguration accordingly fails to limit access to external resources or gives superfluous permissions to accounts. Attackers will exploit this weakness to illegally leak, steal user data and gain unauthorized access to accounts.
6. Vulnerable and Outdated Components
Web apps are also vulnerable to cyber threats if developers don’t know versions of used components in the back-end and front-end. Besides, this defect arises when components are unsupported, outdated, misconfigured, or irregularly examined for vulnerabilities.
7. Identification and Authentication Failures
This refers to failures invalidating the user’s identity, establishing secure authentication, and managing sessions. This security risk shows up when web applications allow default, known-to-be-weak passwords, use ineffective multi-factor authentication, and more.
8. Software and Data Integrity Failures
The OWASP list has recently added this new flaw. It arises when the app’s infrastructure and code fail to secure software and user data from integrity violations. This is because the app either depends on untrusted libraries, plugins, and modules or permits automatic updates without verifying integrity beforehand. Attackers may accordingly gain unauthorized access, upload malicious updates, and compromise systems.
Recommended reading: 6 WordPress Security Issues: Cybersecurity Risks of Managing
9. Security Logging and Monitoring Failures
Logging and monitoring is the process of tracking and recording all data and incidents occurring within the system. Failures in logging and monitoring mean you possibly fail to identify defects that firewalls or scanners hardly discover.
This vulnerability is pretty common. But it’s considered challenging to detect unless organizations experience the failure and hardly fix it. Not to mention that logging and monitoring mostly involve interviewing whether any attacks are discovered during a pen test. This slows down the detection of data breaches and developers’ responses to them.
10. Server-Side Request Forgery (SSRF)
This is the final new security risk described in the OWASP Top Ten List. This flaw occurs when web applications don’t verify the user-supplied URL before fetching data from the source. Although SSRF now receives small attention in Mapped CWEs, Designveloper still wants to warn about its increased severity which is a result of architectural complexity and cloud services.
Best Practices for Web Application Security
Without a well-designed security strategy, your company fails to build web applications effectively. Below are some activities and technologies you should include in such a strategy:
1. Conduct a Comprehensive Security Audit

Carrying out security audits frequently is encouraged to help companies detect possible vulnerabilities in systems promptly. This guarantees web apps are kept from targeted attacks and examines whether teams follow predetermined security practices.
If security audits are not your strength or you want objective assessments, a third-party testing team should take over the job. The team closely works with development teams to conduct one of the following security audits:
- Black box security testing – The testing team doesn’t approach the app’s internal code, but rather examines the system from the outside to discover flaws.
- Gray box security testing – The testing team has limited access to the app’s database and only approaches some key information to detect vulnerabilities.
- White box security testing – The testing team has full access to the codebase to guarantee all practices are followed.
Beyond that, you should consider some popular security testing solutions suggested by Designveloper:
- Penetrate Test: This manual test is designed to test web application security by ethically attacking app systems to discover exploitable flaws. It’s commonly used for checking important apps, especially those going through significant changes.
- Static Application Security Test (SAST): This white-box solution allows developers to scan the whole codebase for vulnerabilities, even without web apps running in an executable state. Apart from automated testing techniques, this approach also requires manual reviews to determine whether positives from automated tests are false.
- Dynamic Application Security Test (DAST): This black-box testing approach automatically scans and analyzes web applications to detect flaws. But it’s only best suitable for solving low-level defects (i.e. injection flaws). If you want to examine medium-risk and high-risk applications, it’s better to combine this solution with other manual testing methods.
After security audits, development teams start evaluating the impacts of vulnerabilities and decide which flaws need fixing first.
2. Guarantee Data Encryption
Encrypting user data is essential even when they’re transferred between the user’s browser and the server or when they stay at rest.
The BuiltWith statistics indicate that 68.61% of million-traffic websites used SSL/TLS encryption in 2021. This cryptographic protocol encrypts and allows all data to flow between the visitor’s app and your system safely. The web application requires strong encryption that can be achieved from RapidSSL certificate, Thawte SSL certificate, GlobalSign SSL Certificate, etc. All these SSL certificates are available from resellers at the lowest price.
Further, your company needs to follow encryption standards to mitigate back-end interventions in data at rest. Some effective activities to secure such information entail encrypting confidential data with robust algorithms and storing them in secure, separate databases. In addition, your company should consider investing in strong network firewalls and infrastructure security.
3. Monitor Real-Time Security
Your app needs perpetual protection measures that help manage security and identify vulnerabilities automatically in real-time. Some common security tools to help you do so consist of:
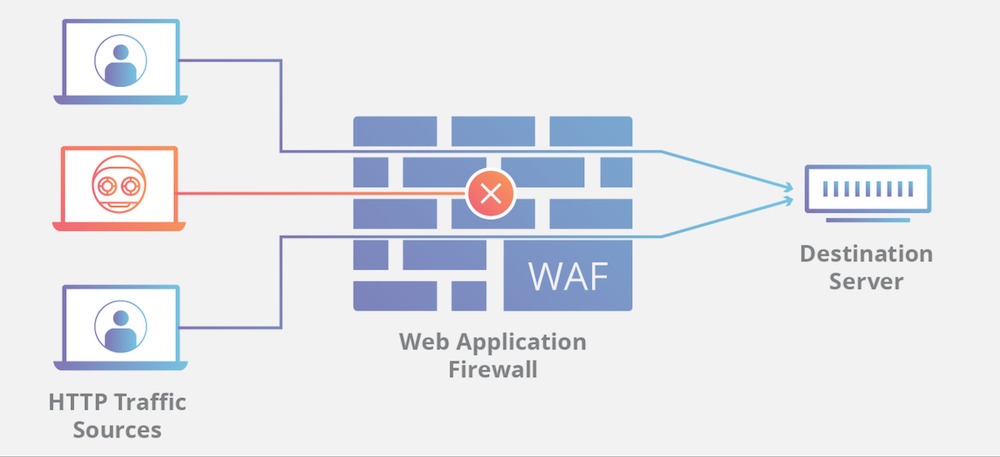
- Web Application Firewall (WAF): A WAF protects your web app from hostile HTTP traffic by establishing a filter between such malicious sources and the targeted server.
- Runtime Application Self-Protection (RASP): The RASP technology works on the webserver and automatically evaluates behaviors on your app. In case attack vectors are detected, the technology blocks such malicious activities and ends sessions.
- Application Security Management Platform (ASMP): An ASMP is integrated with your mobile app to manage multiple protocols (e.g. FTP, TCP or SOAP) and prevent the app from unusual behaviors or attacks in real-time.
Each tool works best in particular situations and also accompanies potential drawbacks. As per your security demands, you can select proper tools or use more advanced technology to best support your 24/7 monitoring of the app.
4. Implement Proper Logging Practices
We mentioned how important logging and monitoring are in the context of cybersecurity. Without proper logging and monitoring practices, you don’t know exactly what occurs at what time and why or how the incident happens. Consequently, you may ignore vulnerabilities, albeit minor, and confront the daunting task of tracking their causes and making post-threat forensics. To implement logging practices effectively, you should use logging and monitoring tools such as PaperTrail, Linux Syslog, or ELK stack.
5. Regularly Follow the OWASP List of Common Vulnerabilities
Sometimes, there are new vulnerabilities incurred without developers knowing because they appear rare or completely new. In such a case, continuously checking the OWASP list is a necessity to help you update your knowledge about such threats. The list also showcases which vulnerabilities are currently dominating. This hence supports you to pre-equip your web applications with higher security so that they can resist such serious vulnerabilities.
6. Apply Security Hardening Techniques

Security hardening is a series of techniques, practices, and tools to eliminate possible vulnerabilities and cement the web app’s security layers. Here are something you should consider to condense your app’s security:
- Maximize script execution time: Depending on your web app’s usage purpose, you can define the maximum script execution time. This time identifies the length of a certain script operating on the web server. So maximizing the time can reduce the possibility of outside attacks.
- Disable extensions or modules: One way to mitigate the attacked area is inactivating extensions or modules that your apps rarely or never use on the webserver.
- Build a robust content policy: Strengthening a content security policy foils malicious infections.
7. Test Web Apps Frequently, Update Security Releases
No web apps have perfect security. And we have to admit that along with the increased advancement of security techniques and tools, hackers also become better. It means they can always find ways to discover and exploit your app’s weaknesses.
There are many ways for you to do this, but one of the most important ones is using a website security test tool. These tools can scan your website or web application for security weaknesses automatically and even generate reports for you. You need them to uncover and neutralize threats to your web applications.
So testing your apps continuously and updating security releases for all servers is a must to diminish attacks from bad people. This procedure can be carried out with automated tools or through a manual review. Moreover, developers can use package managers to automate the process of discovering, configuring, and installing external dependencies to solve your security problems.
Conclusion
The worldwide web app market, especially PWAs, records a compound annual growth rate (CAGR) of 34% over the forecast period 2020 – 2026. This means the possibility of more vulnerabilities faced by web apps is respectively higher. Therefore, one imperative of organizations now is to pay more attention to web application security to make sure it works against potential vulnerabilities. However, we Designveloper acknowledge that there’s no perfect security method. So continuously planning, testing, and upgrading your app’s security is a necessity.